While modern SDKs and libraries abstract much of the complexity of OAuth 2.0, a good understanding of the underlying authorization request structure remains essential for developers. When issues arise, such as unexpected redirects, token rejection, or other error messages, having insight into the raw request helps in troubleshooting. hello world
This mostly depends on what type of developer you are, of course. It's like opening the hood of your car to diagnose a problem. You don't have to be a mechanic or even an engineer to understand every little detail of your car's engine. But being able to determine whether the engine is overheating because of insufficient coolant or the car won't start because a battery cable has come loose can help you speed up the troubleshooting process, sometimes even without the need for expert intervention.
<include srx=”ebook-ads/oAuthGuide” />
The Authorization Request Under X-Ray
I assume you have a basic understanding of OAuth 2.0. If not, you can read a quick introduction to the authorization framework and its flows. If you want to go more in depth, check out OAuth 2.0 and OpenID Connect: The Professional Guide.
While this article mentions OAuth 2.0, you will also find details related to OpenID Connect and other OAuth extensions. This is because it’s very common to see the two protocols interconnected. After all, OpenID Connect is nothing but an OAuth 2.0 specialization.
It all starts when a client application redirects a user's browser to the authorization server to begin the authorization process. The authorization request is usually a GET HTTP request sent to the authorization endpoint of the authorization server, although it may be a POST HTTP request too.
The following picture shows a typical authorization request:
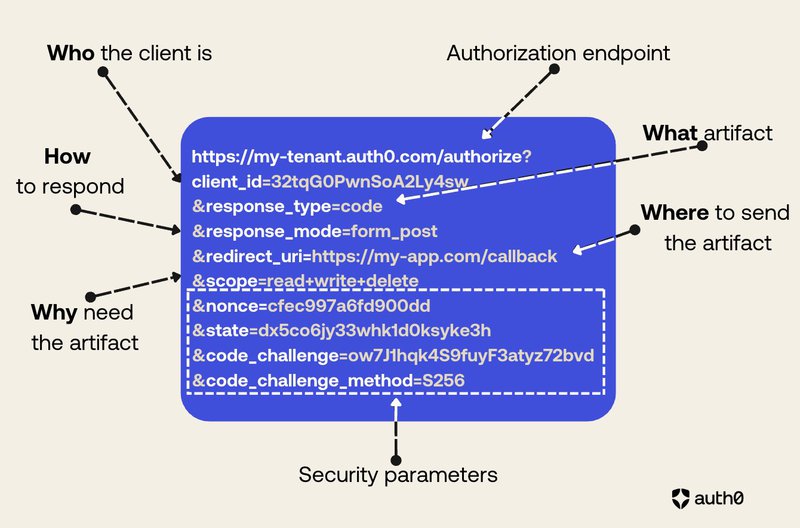
As you can see from the picture above, the authorization request structure expresses what the client application wants to achieve. You can highlight the main elements of its structure with something vaguely reminiscent of the 5 Ws of journalism:
- Who is making the request?
- What artifact is requested?
- How is the artifact returned?
- Where will the artifact be sent?
- Why is the artifact needed?
In addition to these fundamental elements of the request, there are other elements that help improve its security posture.